
Exactis, a US-based marketing firm you didn’t know existed, discovered earlier this year that it was storing its database of 340 million customer records on a publicly accessible server. The security firm that located the risk told WIRED it was one of the most far-reaching databases of information it had ever seen—the entirety of which was easily vulnerable to attack.
Exactis’ failure presents obvious parallels to Equifax Inc.’s 2017 breach of 143 million US customers’ Social Security Numbers and much else. Disasters like it are why Senator Elizabeth Warren is championing an Office of Cybersecurity at the US Federal Trade Commission to enforce higher data protection standards for handling consumer records.
The core principles of Senator Warren’s proposed Data Breach Prevention and Compensation Act of 2018 (DBPCA) became a reality in the European Union as of last May. For EU members it’s called the General Data Protection Regulation (GDPR)—and the LeanIX blog has reported on it from conception to reality plus hosted compliance seminars with those like Andreas Bosch from McKesson. But seeing that many EU companies grapple with its terms, are American enterprises likely to also struggle if/when their turn to submit?
And more specifically, must Enterprise Architects re-think operations to prepare for whatever wave of intensified scrutiny is coming their way?
Let’s check some of the DBPCA’s key points to see how LeanIX’s IT management tool could protect American firms once the Cybersecurity authorities come knocking...
Sec. 3. (b)(1)(B)(i)(I)(aa) asset management, including—
(AA) an inventory of authorized and unauthorized devices;
(BB) an inventory of authorized and unauthorized software, including application whitelisting
If you are a business receiving information from the public, then the proposed DBPCA requires you to actually have what it takes to store that information safely. To do so, the Office of Cybersecurity wants details of your system and network security measures—in particular: “an inventory of authorized and unauthorized devices; (BB) an inventory of authorized and unauthorized software, including application whitelisting; and (CC) secure configurations for hardware and software”.
What this means is that you better have full access to high-quality data across your IT portfolio to evaluate compliance readiness. And if you don’t, now is a perfect time to finally digitalize your database to an application like LeanIX to make such a flexible overview possible.
Transferring (or, as we say, “modernizing”) bulk amounts of system data to evaluate the security of your IT landscape can be managed in LeanIX from a variety of sources. If starting entirely from scratch, data in Excel sheets can be fed automatically into new or existing “Fact Sheets”—the single-page banks of information which make up the LeanIX analytics network.
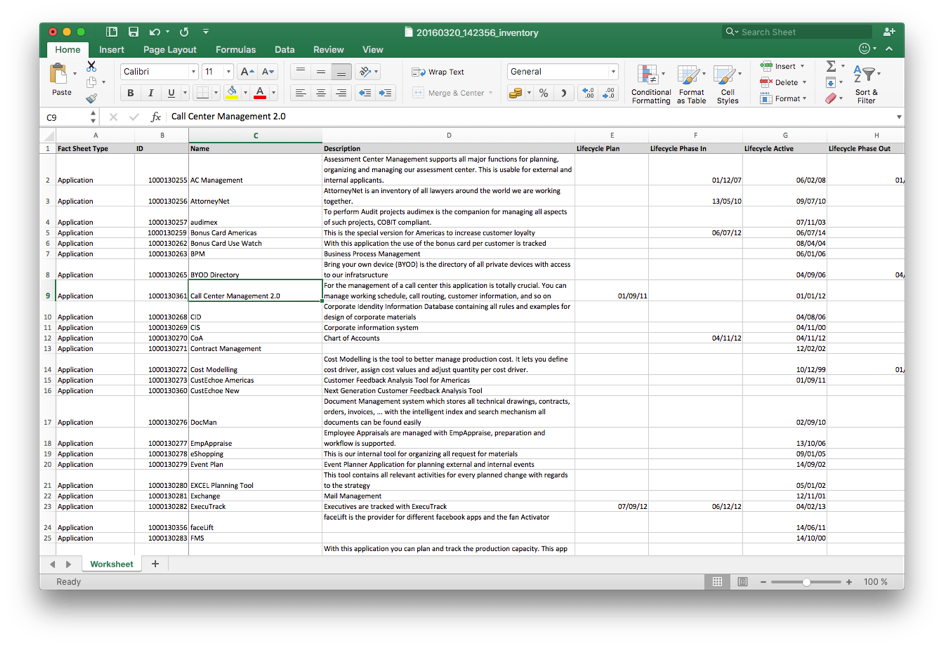 Image 1: An Excel file structured to be imported into LeanIX. In this example, unique applications are prepared according to “Fact Sheet Type”, “Name”, “Description”, and various stages of their “Lifecycle”.
Image 1: An Excel file structured to be imported into LeanIX. In this example, unique applications are prepared according to “Fact Sheet Type”, “Name”, “Description”, and various stages of their “Lifecycle”.So, to ensure the right data is fuelling your security reports, LeanIX administrators have certain tools at their disposal to pull only the best data to gauge security preparedness…
Fact Sheet Completeness
Yes, as the title quite literally suggests, the “Completeness” of a Fact Sheet is one way to safeguard against junk application data. Completeness is calculable in LeanIX based on which Fact Sheet fields you choose to make optional or mandatory, and the percentage is determined by the “weight” (the importance) and “status” (the applicability) given to each element. Each application in your landscape is meant to be advantageous for its own reason, so if you believe one presents greater value for (*hint* *hint*) the purposes of customer data protection, you can load it accordingly.
Quality Seal
One reason LeanIX is designed to be a collaborative tool is to maximize information-gathering efforts. Increased participation nevertheless requires everyone to be following clear quality assurance marching orders. The LeanIX “Quality Seal” is a mechanism to protect Fact Sheets from slipping into irrelevance by automating reminders to those responsible for its maintenance. Quality Seals appear on the top right of a Fact Sheet and will “break” if past their review date. A broken seal will trigger a surly mail to all responsible parties (thereby allowing you to appropriately level blame for jeopardizing your company’s integrity).
Surveys
Everyone loves beautifully qualified, up-to-date application data. So give the gift of love today by delivering configurable surveys, en masse but without individual mailings, to let your teammates (wherever they may be) answer questions on how to revise Fact Sheets with current information. More will be discussed on surveys in the proceeding blog post, but consider the particular benefits of surveys in relation to IT security in the image below (“Assessment of application security according to IT-Grundschutz”)
Above are six basic but critical questions regarding applications that are almost impossible for an IT manager to ask when lost in layers of company communications channels. In theory, such an assessment of application security can mobilize participation from an entire organization. Teamwork!
(cc) application management, including—
(AA) continuous vulnerability assessment and remediation;
After foraging for precious data in the badlands of your pre-LeanIX optimized enterprise, you are now ready to open your (comically undersized) bindle to check the goods. Proposed Sec. 3. (b)(1)(B)(i)(I)(cc) demands vigilant “application management”, and quite specifically, it wants (AA) “continuous vulnerability assessment and remediation”.
An agile approach to application management is a way to proactively prune IT landscapes of technologies with the potential to destabilize organizations. Knowing the relationships between your operation’s applications, how each depends upon the other, and what resources are needed to support their ongoing performance, is a surefire way to keep the gates to your confidential data shut.
To quote my EA forebears: “it is crucial to identify and understand which underlying technologies exist in their lifecycles and any software dependencies”.
Consider how the following reporting tools in LeanIX enable the precise vulnerability assessment and remediation needed to safeguard your company's data...
Application Landscape
One of a number of report types offered by LeanIX is the “Application Landscape”, a configurable view of the state and interlinking relationships of applications across an operation.
Drawing from information contained inside Fact Sheets, users can create visual tables of information from an assortment of filters, many of which are designed specifically for security assessment.
Applications are sorted, at the highest level, by business service plus the five stages of operating “Lifecycle” (from “Plan” to “End of life”). The report is filtered deeper to include results with a broken “Quality Seal” and if the application is connected to the usage of “Customer Data”. As you can see, there are several applications in red. This is an EA’s cue to investigate further what available security patch or software upgrade is needed to stop bleeding and prevent system infection.
Backdoors to customer data can surface in many locations, not just within applications dedicated to its storage. It’s therefore important to use all available Application Landscape reporting views and filters to find improvements.
Application Matrix
The Application Matrix reporting tool, as seen in the image below, can separate applications by geography and link distant data objects to determine shared business functions. In the snapshot below, vulnerabilities are being viewed by “Business Criticality” and filtered according to “Data Quality: Quality Seal broken” > “Data Objects: Customer Data”.
So, it appears that there are numerous applications shared by many services in the organization with broken quality seals (and thus high-potential security risks). Let’s look deeper at one of these applications to see what should be done...
There are several things to consider in the Fact Sheet for “Bonus Card Americas”. Used by business units in Brazil and the United States, Bonus Card Americas’ agreement is set to end halfway through 2019 without any documented plan for continuation.
As it is an application marked as supporting customer data and the integration of “Customer Loyalty Information”, will its phase-out strand confidential information? As well, is there a reason the operation chose to prolong support for other regional versions of Bonus Card Americas (e.g., “Bonus Card Europe”)?
Is this an oversight the Cybersecurity Office will want to know more about?
To remedy this problem, it’s suggested you look at who is responsible for updating the information on this Fact Sheet (spoiler alert: it’s been neglected).
Three users: two “Responsibles”; one “Observer”. None of them have visited the page since 2015 to update its data. This is why the Completeness of this Fact Sheet is at “45%”.
Quick-win: Request an update via a survey, and align answers with Responsibles from other regions.
Closing thoughts
The public is paying attention, more than ever, to the security capabilities of those they must trust (in many cases, without any alternative option…) with their information. Unassailable data protection is no longer an added value—it is the expectation.
However, while it is problematic to predict the final parameters of proposed government policies, an IT infrastructure integrated with agile Enterprise Architecture can grant you the visibility and flexibility to help your business react faster to regulatory standards.
Upgrading to a digitalized tool is the first step to properly receiving and storing the high-quality data needed to base compliance insights. Follow up this knowledge with comprehensive reporting mechanisms to discover how to make this information work for you.



