
Cyber security and compliance become harder and more expensive every day. Our professional services consultant, Norma Arrazola Herrera, looks at how holistic enterprise cyber security can be enhanced by the Gartner Pace layer model.
As digital transformation accelerates into continuous transformation, maintaining holistic enterprise cyber security grows more complex. Likewise, scaling globally means navigating a variety of new data privacy laws and regulations.
Think about the vast amount of data flowing through the hundreds or even thousands of applications in your portfolio. This data not only interacts with multiple interfaces, but it’s stored in siloed components in multiple geographies.
Finding, classifying, and visualizing all that data can be arduous. With GDPR, for example, you need to know every app that touches Personal Identifiable Information (PII). If you're audited by regulators, or a customer asks you to delete their information, you must be able to locate specific data promptly.
Securing your application portfolio against cyber threats requires thorough analysis and prioritization. Yet, it’s not feasible to secure every app your organization uses to the same degree, nor is it necessary.
Some applications are more critical than others and pose different degrees of risk to data privacy and business processes. Companies have to focus security efforts on the applications that enable the most business-critical capabilities.
That becomes increasingly difficult as IT infrastructures grow more labyrinthine. This is particularly true when decentralized software purchasing means that IT doesn’t always know exactly what the business is using.
The best way to ensure sufficient security and compliance in the current era is a deeper, more comprehensive approach: holistic enterprise cyber security.
What Is Holistic Enterprise Cyber Security?
Holistic enterprise cyber security is a cross-sectional approach where risk management is carried out holistically across all an organization’s applications, business capabilities, data and technology.
This approach thinks of enterprise architecture in terms of layers:
The business layer consists of your company’s business capabilities (what you, as a company, need to do to be in business), including shipping and receiving, customer service, inventories, payrolls, accounts payable and receivable, etc
The data layer consists of all the data your organization has, and the models, policies, and standards that govern which data is collected and how it is stored, arranged, integrated, and utilized
The application layer consists of all the software applications in the organization’s IT architecture and how they interact with each other
The approach begins with the creation of a comprehensive inventory of all of your applications. This will clarify which business capabilities the apps support, what data they contain, and help prioritize your security efforts to ensure the continuity of your critical business capabilities.
Using The Gartner Pace Layer Model For Holistic Enterprise Cyber Security
For example, you might have an application that enables employees to place lunch delivery orders from nearby restaurants. While this might be a popular app among workers, it isn’t a critical enterprise cyber security concern.
You need to focus security efforts on the applications that are necessary for you to operate and stay profitable. To determine which applications those are, however, you have to map out your business capabilities and do an assessment to find which ones are most business-critical.
The most effective application strategy to do this is with the Gartner Pace layer model. Pace is an industry-standard way to categorize, manage, and govern applications.
Pace consists of three core application types:
- business change
- differentiation
- innovation
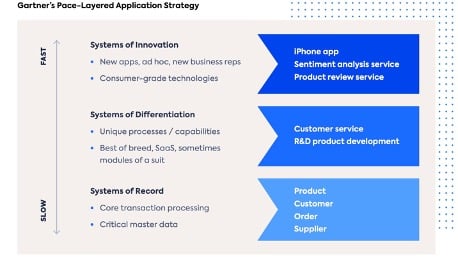
Securing Your Application Portfolio
After determining which apps enable your most-important business functions, you then have to assess the enterprise cyber security of those apps. You will need clarity on which security controls are in place and what types of data the applications are using.
The data objects an application interacts with are key to determining the security and compliance requirements of the app, and whether those requirements are being met.
Ask:
- What is the level of confidentiality of this data?
- Which applications make use of this data?
- What is the risk of data leakage?
For example, if any applications touch data objects that contain PII information, that application must be compliant with GDPR.
It's also critical to examine all the interfaces that connect apps and components across your IT architecture. Interfaces touch all of the data objects moving between them, and they could contain security vulnerabilities or be out of compliance.
Ask:
- How will the business be affected if there is a breach through an interface?
- Which security protocols are in place?
- How sensitive is the data being transferred through the interface, and which level of integrity should it have?
Lastly, you must examine all of your IT components to determine where all of your different data types are physically stored, and ensure your security measures, protocols and processes are sufficient and compliant.
Ask:
- How old is the component?
- Has it received the latest security patches and updates from the vendor?
- Does it still comply with modern regulations?
That sounds great, but how do I do all that?
In order to prioritize which applications are vital to your holistic enterprise cyber security strategy, you need to map your entire enterprise architecture. You need visibility on how all of your business capabilities, applications, data objects and technology interact with and support each other.
Unfortunately, a lot of this information is hard to find, and much of your data is likely in siloes. Traditionally, enterprises have collected this information manually, but running around asking different departments for information on their systems and recording it in spreadsheets is inefficient.
It’s time-consuming to collect and analyze the information, and the process often results in data gaps, outdated information, and human error. This means you’re more likely to miss vulnerabilities and compliance lapses.
Luckily, LeanIX has your back...
How LeanIX Enables Holistic Enterprise Cyber Security
LeanIX helps you combine your security and compliance practices with robust enterprise architecture management, so you can adopt a holistic enterprise cyber security strategy.
With LeanIX you can:
- Map your entire enterprise architecture to determine which apps support which critical business capabilities
- Visualize how data objects move between apps and through interfaces
- Pro-actively manage technical debt from outdated components
- Have a single source of truth as an information hub for all stakeholders
With out-of-the-box reporting and diagramming capabilities, intuitive visualizations of interfaces and data objects exchanged by applications, and tech obsolescence analysis, you no longer have to deal with multiple teams using multiple visualization tools for cyber-security. Data is automatically imported through open APIs and out-of-the-box integrations to solutions like ServiceNow.
LeanIX also optimizes data collection across the enterprise by automatically sending questionnaires to departments as often as necessary. You can automatically track who has completed their surveys to ensure your data is reliable and up to date.
Typically, you'd have to track stakeholders down in person, on the phone or through email to get them to provide the information you need. LeanIX takes the burden off your plate, and once you get the data you need, the reporting and diagrams are updated automatically.
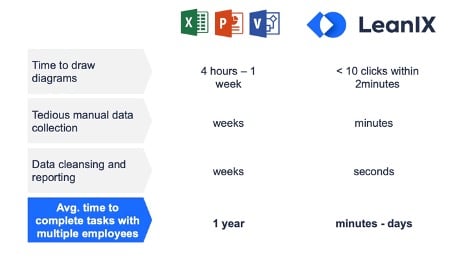
LeanIX has helped many organizations ditch the spreadsheets and adopt next-level holistic enterprise cybersecurity. See below for an overview of what we can do for you and how to take the first step:


