
As the requirements mentioned in our previous posts in our series on IT Security Management with LeanIX Survey clarify, a purely technical approach alone is not enough. In the current business environment, it will hardly be possible anymore to completely seal off one’s own IT landscape. Companies should instead follow a lean IT security management approach that makes it possible for them to iteratively improve their IT security:
1. Determining the responsibilities and roles relevant to IT security
A clear role distribution in IT security is considered a critical prerequisite for all other activities: Who is responsible for a particular application? Who implements technical requirements? Who has to be informed in case there is a security incident? In practice, the roles and responsibilities at companies are often defined according to techniques such as “RACI”2.
An enterprise architecture solution such as LeanIX offers the required support for this. In LeanIX, clear responsibilities for fact sheets (e.g. for an application or a process) can be set up and continuously maintained. Quality mechanisms ensure that the data stays current. This has the major advantage that current data will be available in the right context in case of a security audit or incident, e.g. for a concrete application such as “Executive HR” (see figure 8). Inquiries about particular information can then be handled appropriately.
2. Classification of the criticality of information
In general, the goal of IT security is to offer the best possible protection of information. However, in the digital age there is hardly any company that can still guarantee 100-percent IT security; instead it has to focus on controlling those areas where a data and security breach or cyber attack could create the largest problems and the most negative results. Current classifications evaluate information and data on a four-step scale from “public” (data can be made public without negative results) to “confidential” (data that can damage individuals or the company).
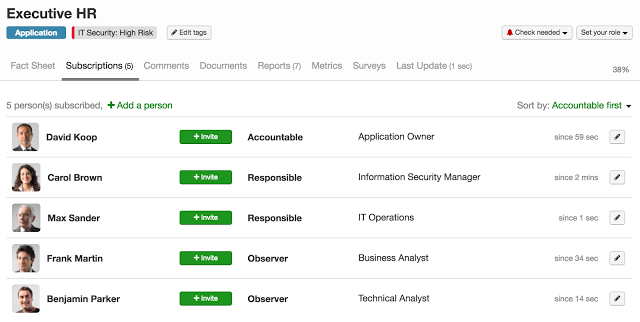 Different IT security roles can be stored with LeanIX fact sheets
Different IT security roles can be stored with LeanIX fact sheets
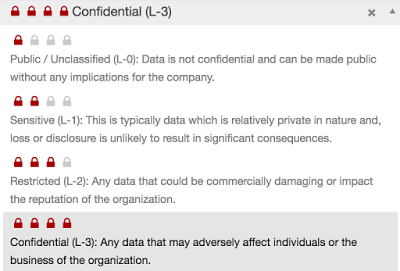 Evaluation of the data criticality in LeanIX
Evaluation of the data criticality in LeanIX
3. Identifying critical applications and dependencies
The next step is about understanding which applications are particularly relevant to IT security. For example, this could be systems that are used to manage personal customer or staff data or for the archiving of sensitive documents (contracts, offers, design drawings, etc.). LeanIX responds to these complex questions with simple visualizations, e.g. in heat maps. This makes it possible to answer important questions at a glance: Which applications use sensitive data objects? Which business areas are affected? What effects does a failure have on other applications and processes?
In addition to the affected data, the financial consequences in case of a failure are another central criterion for determining the security relevance of applications: Does the application directly affect the revenue? Is this “only” a supporting system? All of this information is easy to track and query in LeanIX.
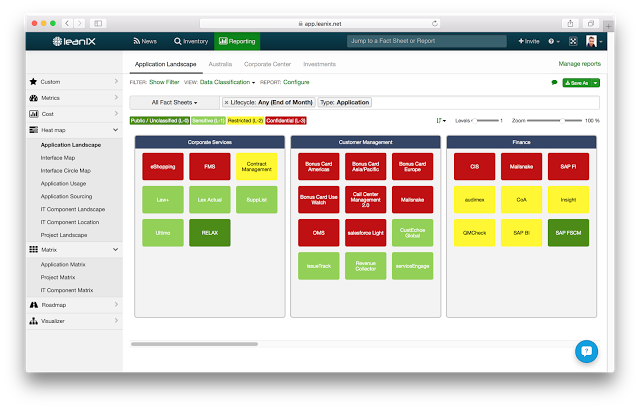 Visualization of applications that work with critical data
Visualization of applications that work with critical data
4. Making security specifications transparent
Often companies already have numerous documents that define security guidelines. They frequently range from generically applicable guidelines to concrete security controls, which may be used as the basis of audits, for example. These documents thus represent the target state for security measures. However, experience shows that it is often unclear when and which document should be used or where the most updated documents can be found. In LeanIX, documents are stored directly with the fact sheet, e.g. with an application. This makes the specifications available to the right employees in the right place.
| Find out more: Request your free LeanIX trial now! |  |
5. Continuous updating of the IT security data through automated workflows
Modern IT systems – especially if they are integrated and connected with external systems and platforms in the course of a constant digital transformation – are undergoing a continuous change. That is why the IT security management also has to be constantly adapted to the new requirements. It is not possible for the central office to order IT security; instead, the security has to consist of a continuous process that has to be implemented together with the company employees.
As shown in the case study above, it is possible to perform regular online surveys about topics relevant to IT security with LeanIX Survey. It gives companies the ability to keep all required
IT security data updated over the long term. The great advantage lies in a significant acceleration of the data compilation and making the collected data directly available in the right context. Fact sheet segments can be included in the survey and this makes their updating even more convenient. With further functionalities such as dependent or calculated fields, risk indicators can be collected and made transparent. This ensures that IT security is improved on a permanent basis. Then the collected data also forms the foundation for current and precise statements related to security audits to check the adherence to compliance specifications or IT security standards, such as the IT baseline protection or ISO 27001.
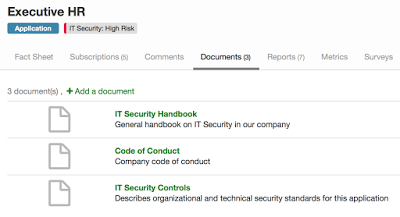 Security guidelines can be stored directly with the fact sheet (e.g. an application).
Security guidelines can be stored directly with the fact sheet (e.g. an application).
Summary
A consistent company-wide IT security strategy and a streamlined IT security management approach that builds on this only work if all relevant processes and workflows are oriented along those lines throughout the company. This requires everyone’s decentralized cooperation. The LeanIX Survey Add-On simplifies and accelerates formerly work-intensive, manual data compilation processes.
We hope you enjoyed our blog series on IT Security Management with LeanIX Survey! Please download the white paper for even more detail on the subject.



