
Since the Log4Shell vulnerability became public, companies have been working quickly to fix vulnerabilities in their own systems while also scrutinizing their application portfolio to understand their overall exposure.
To assist LeanIX customers on this front, our team of researchers continue to collect information on the remediation efforts of the top 20 SaaS vendors used by our customers. We publish the information collected in LeanIX's SaaS Catalog, which is available to LeanIX APM customers.
Our dedicated team of researchers keeps the SaaS catalog up to date with accurate information on a wide range of SaaS applications. This information includes application description, product category, SSO, hosting, and so on.
Using the SaaS Catalog, customers can quickly determine, on a daily basis, the Log4Shell remediation status for specific SaaS applications. The catalog also provides links to sites and posts where SaaS application providers have published information on the vulnerability, along with any additional information about the vulnerability we find.
Where can customers view this information?
LeanIX APM customers who have enabled the “SaaS Catalog” or “SaaS Discovery” feature can access this information in several ways.
- Via the Application Fact sheet detail page by clicking “SaaS Catalog” on the right side panel:
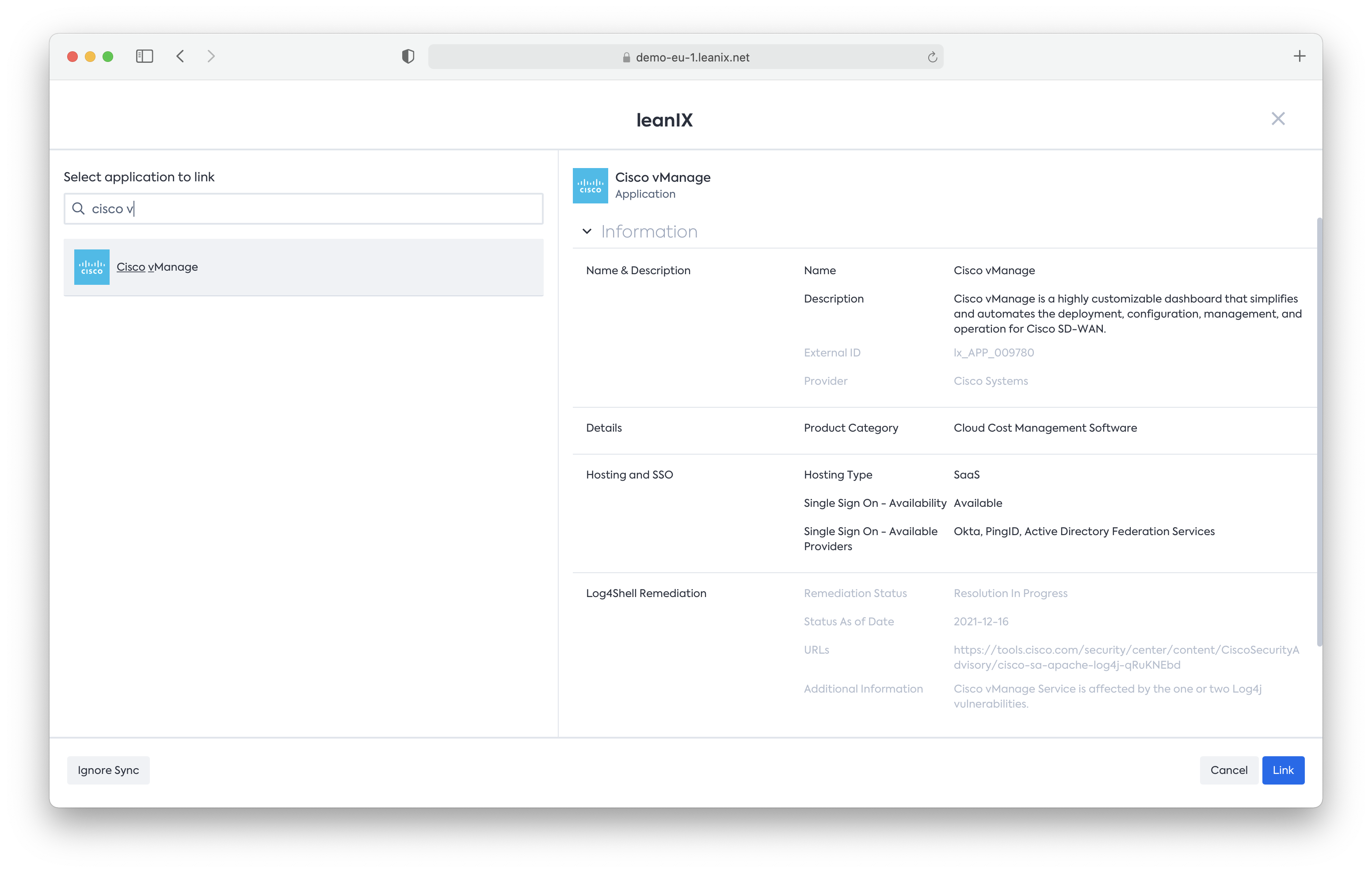
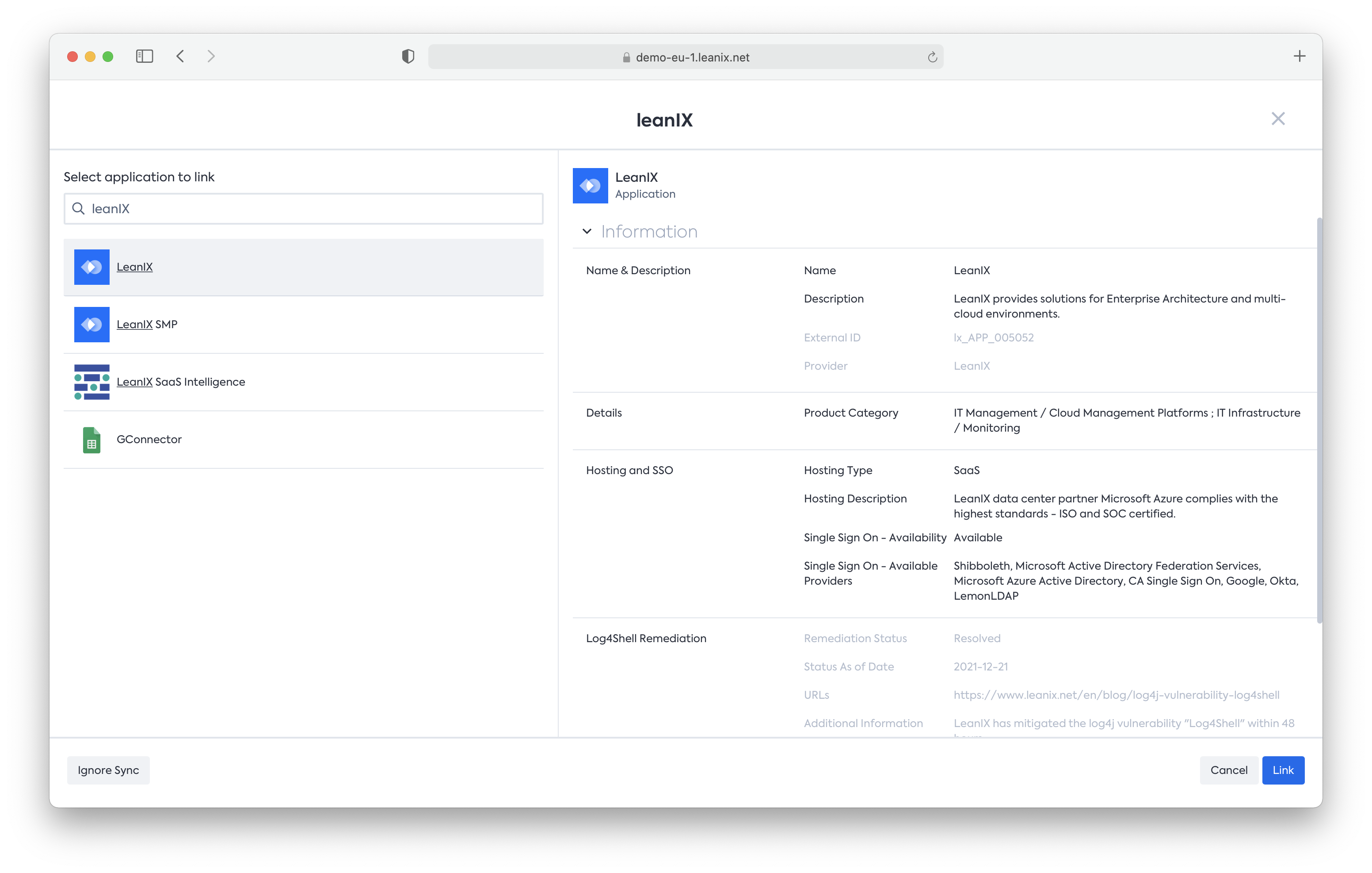
- Via the Inventory page by clicking on “SaaS Catalog” on the right side pane, you will find this information in the Preview section of every recommendation from the SaaS Catalog:
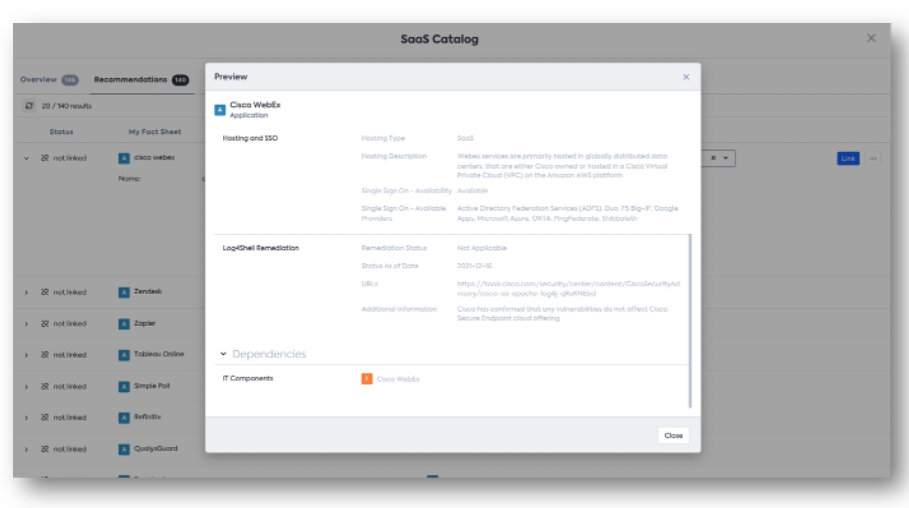
What our Log4Shell research uncovered
We catalogued Log4Shell remediation data for over 200+ SaaS Applications. In the process we found that most vendors continue to work diligently to remediate this vulnerability as it evolves.
We also found the following regarding Microsoft and Oracle:
- Most Microsoft Applications have not been affected by this vulnerability.
- Oracle strongly recommends that customers apply the updates provided by their Security Alert.
- Product releases that are not under Premier Support or Extended Support were not tested for the presence of vulnerabilities addressed by this Security Alert. However, it is likely that earlier versions of affected releases are also affected by these vulnerabilities.
- Oracle recommends that customers upgrade to supported versions.
- Using Lifecycle Catalog, our TRM customers can check if their Oracle Applications are supported or not


