CONTINUED
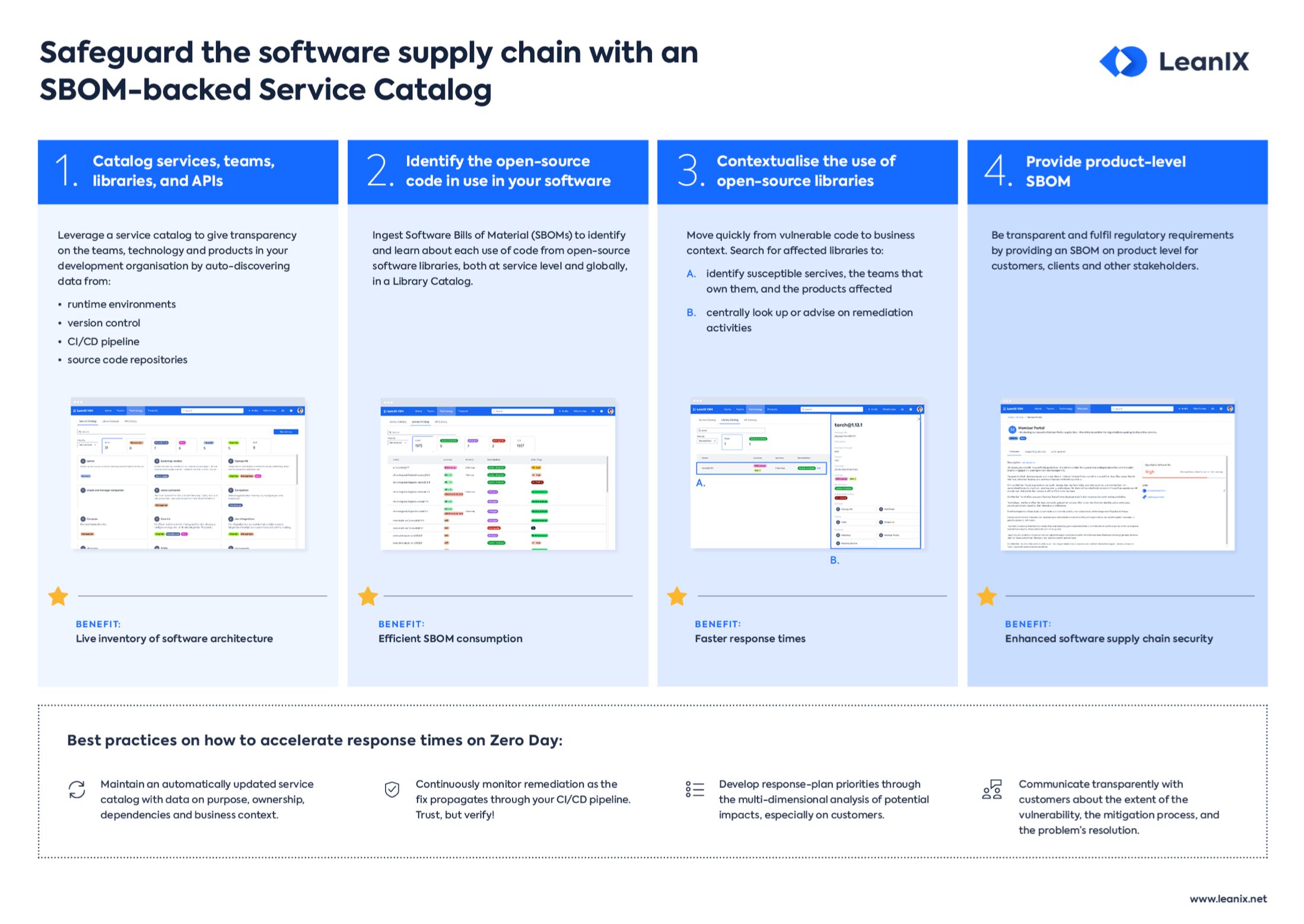
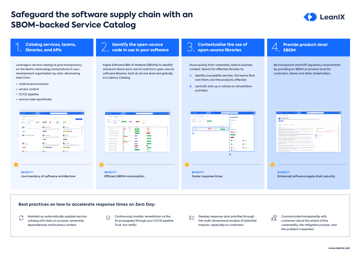
4. Leverage Software Bill of Materials (SBOMs)
The role of SBOMs in tracking and managing components
A Software Bill of Materials (SBOM) is a comprehensive list detailing every component, dependency, and piece of metadata within a software product.
In the complex landscape of modern software development, where products often rely on numerous third-party components, an SBOM acts as a critical tool for transparency and security. It allows organizations to quickly identify the components they're using, track potential vulnerabilities, and manage updates.
In essence, an SBOM provides a clear view of the software's composition, enabling proactive security management.
Example: Using an SBOM to identify the use of a vulnerable library version.
How to implement it in your role?
- CTOs: The CTO champions the adoption and regular updating of SBOMs, recognizing their value in enhancing software supply chain security.
- Developers: Developers contribute to the SBOM by documenting the components and libraries they integrate into the software.
- Architects: Architects ensure that the structure of the software is well-represented in the SBOM, providing clarity on how different components interact.
- Project Managers: Project Managers oversee the creation and maintenance of the SBOM, ensuring it's kept up-to-date throughout the software's lifecycle.
📚 Related: Why do SBOMs Matter?
5. Continuously monitor and patch vulnerabilities
Monitoring new vulnerabilities and assessing impact
The digital threat landscape is in constant flux, with new vulnerabilities emerging daily. Organizations must adopt a proactive stance, continuously monitoring for these vulnerabilities.
Once a potential threat is identified, it's crucial to assess its impact on the organization's software and broader infrastructure. This continuous vigilance ensures that organizations can respond swiftly, minimizing potential damage.
For organizations looking to optimize their software supply chain and streamline their processes, Value Stream Management offers insights into best practices and methodologies.
Example: Being alerted to a zero-day vulnerability in widely-used software.
How to implement it in your role?
- CTOs: The CTO sets the direction for continuous monitoring, emphasizing its importance and ensuring that the necessary tools and resources are in place.
- Developers: Developers stay informed about the latest vulnerabilities, especially those that might affect the components they work with. They play a crucial role in the initial response to potential threats.
- Architects: Architects assess the potential impact of vulnerabilities on the overall system, providing insights into potential weak points and areas of concern.
- Project Managers: Project Managers coordinate the organization's response to vulnerabilities, from initial detection to final resolution.
The importance of staying informed in the software supply chain space
In the rapidly evolving landscape of software development, the security of the software supply chain has emerged as a paramount concern.
As we've discussed throughout this guide, there are numerous best practices that organizations can adopt to secure their software supply chains.
However, beyond these practices, it's crucial for organizations to stay informed and updated with insights from leading entities in the space.
These entities provide valuable research, guidelines, and perspectives that can shape and enhance an organization's approach to software supply chain security.
- CISA's guidelines for developers: The Cybersecurity and Infrastructure Security Agency (CISA) offers a comprehensive guide aimed at developers. This resource underscores the importance of securing the software supply chain and provides actionable insights for developers to enhance security throughout the software development lifecycle.
- Google's insights on software supply chain defense: Google, a tech giant with vast experience in software development and security, shares new insights for defending the software supply chain. Their perspective, derived from years of experience and research, offers valuable strategies and considerations for organizations of all sizes.
- Google's perspectives on security: In their Perspectives on Security Volume One, Google delves into various aspects of digital security. This resource provides a holistic view of security challenges and solutions, emphasizing the importance of a multi-faceted approach to safeguarding digital assets.
- CNCF's best practices for supply chain security: The Cloud Native Computing Foundation (CNCF) has released a paper defining best practices for supply chain security. This document offers a deep dive into the challenges and solutions associated with securing the software supply chain in cloud-native environments.
📚 Related: SBOM Time Act, SBOM EO 14028, and SBOM CISA Regulation
Conclusion
In conclusion, while adopting best practices is essential, staying informed with the latest insights from leading entities ensures that organizations are always a step ahead in securing their software supply chains.
As the digital realm continues to evolve, proactive learning and adaptation will remain key to navigating the challenges and opportunities that lie ahead.





/EN/Tools/EA-Maturity-Thumbnail.png?width=260&height=171&name=EA-Maturity-Thumbnail.png)