Change your password, cover your webcam, and grab some popcorn
At a glance:
- Facebook (29 million users affected)
- Chegg (40 million)
- Google+ (52.5 million)
- MyHeritage (92 million)
- Quora (100 million)
- MyFitnessPal (150 million)
- Exactis (340 million)
- Aadhaar (1.1 billion)
It’s wrong to use disasters to help sell a product. But that’s exactly what I am going to do in today’s blog post about the Top Data Breaches of 2018 and the Purely Coincidental Benefits of Technology & Risk Management with LeanIX.
Please forgive. But also please read.
Facebook — 29 million
What Happened: Facebook did not have a good 2018—this much even my Great Uncle Walter knows. 29 million is the reported number of users whose home locations, contact details, search histories, and device data were stolen. Rumour has it that a minor flaw in Facebook’s “View As” feature was exploited by hackers who leveraged it to impersonate users and steal data at an incredible scale.
Technology & Risk Management with LeanIX:
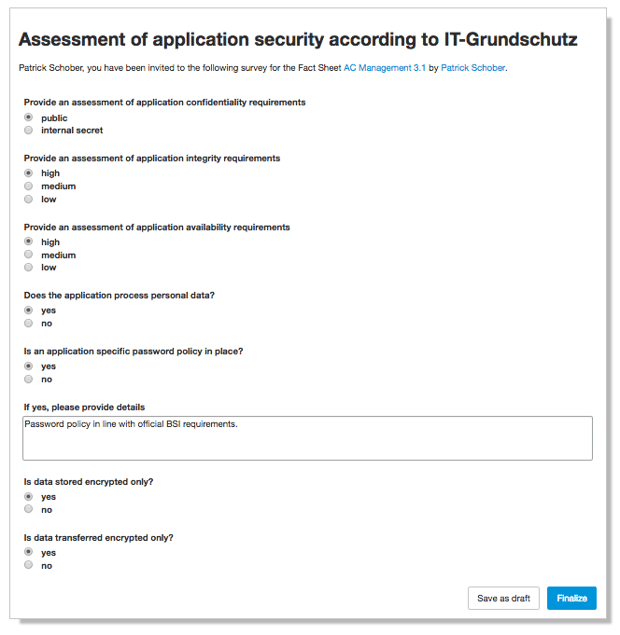
IT Security Surveys are efficient ways to evaluate security readiness by collecting input from large audiences in easy-to-execute formats. Surveys can be assembled using templates or made wholly from scratch based on whatever needs answering. Results are fed directly into LeanIX, and answers can be put into a “calculated field” to tally numerical figures into measurable variables.
Image 1: A LeanIX Survey on IT Security entitled "Assessment of application security according to IT-Grundschutz".
Chegg — 40 million
What Happened: Based in Santa Clara, California, Chegg is in the business of making physical and digital school supplies. Throughout the spring and summer of 2018, it unknowingly trickled out 40 Million shipping addresses and personal passwords to hackers. The company simply told the US Securities and Exchange Commission that an "unauthorized party" gained access to its database of very juicy user data.
Technology & Risk Management with LeanIX:
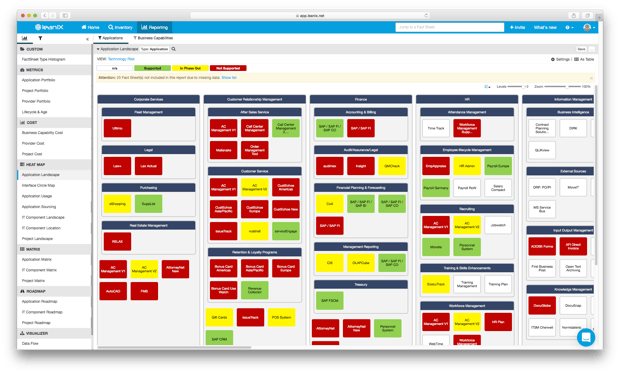
A LeanIX Application Landscape Report shows, in beautiful detail, which Business Critical IT applications are most susceptible to outsider interference. Service lifecycles of technology from all departmental units can be viewed according to numerous states—“Any”; “Plan”; “Phase in”; “Active”; “Phase out”; “End of life”—to spotlight antiquated technology. And if you don’t feel like digging too deeply, there’s a direct “Technology Risk” view that immediately shows your enterprise’s most pressing problems.
Image 2: A LeanIX "Application Landscape" Report.
Google+ — 52.5 million
What Happened: 52 million users—most of whom likely forgot that they had even created a Google+ account—had the details of their lives carted off to the black market. An internal audit compounded by an investigation by the Wall Street Journal revealed that a nasty bug had been spitting out user data for over three years. The second bug in Google+’s API was also discovered in the autumn of 2018.
Technology & Risk Management with LeanIX:
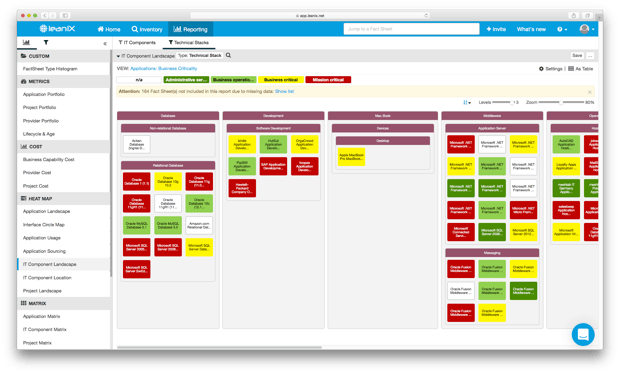
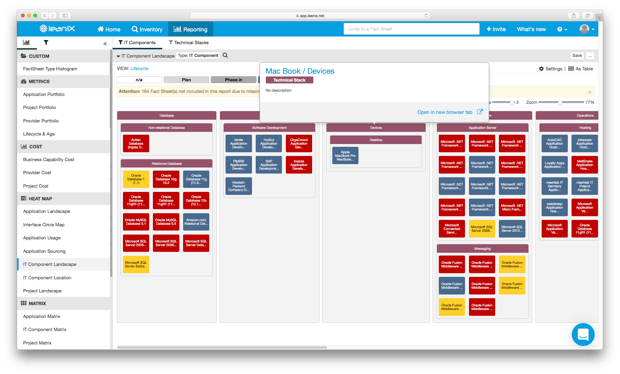
It’s imperative for a global enterprise to maintain technology standards—a list of appropriate applications perfectly aligned to defined security requirements. Modern Enterprise Architecture Management with LeanIX allows IT and Business leaders to see non-standardized technologies with analytics like the following “IT Component Landscape” Report:
Image 3: A LeanIX "IT Component Landscape" Report.
MyHeritage — 92 million
What Happened: A genealogy and DNA testing service called MyHeritage somehow let 92 million account details float away to an external, anonymously-owned private server. The breach was discovered and then shut only after an independent security researcher informed the company that they’d found it while performing a routine patrol. The reasons for it all still appear vague. MyHeritage’s Information Security Team is still trying to figure out how its customer information, all of which were stored remotely and protected by one-way password hashes, was accessed and then transported.
Technology & Risk Management with LeanIX:
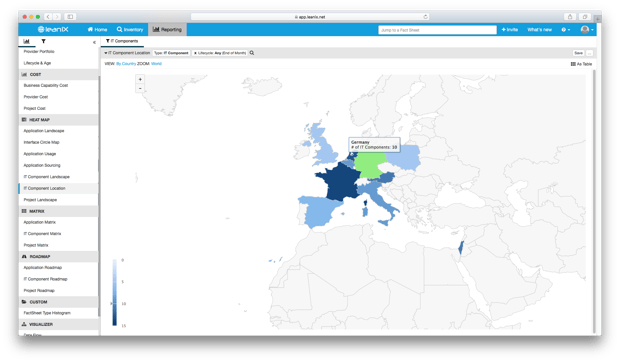
LeanIX’s “IT Component Location” Report can help LeanIX users evaluate the technical/functional suitability of servers and data centers used worldwide by their enterprise.
Image 4: LeanIX's "IT Component Location" Report.
Quora — 100 million
What Happened: Quora, the place where the opinions of strangers can be vaulted above the knowledge of licensed experts, acknowledged that data from approximately 100 million of its users was compromised. Account information, public and private (e.g., direct messages) content, and data from linked networks were part of the loot. According to Quora’s official statement, “a third party who gained unauthorized access to one of [Quora’s] systems” pulled off the heist. And that is all we’ll probably ever know.
Technology & Risk Management with LeanIX:
The twenty largest technology vendors alone provide over a million different technology products—and the details of each one can change in the course of a single day. Flexera’s Technopedia offers a rigorously updated catalog of them all, and with its integration with LeanIX, users can receive synchronously-linked technical updates about their fundamental IT applications.
MyFitnessPal — 150 million
What Happened: 150 million users of MyFitnessPal, a dietary and fitness tracking app owned by Under Armour, are reported to have had the most minute details of their bodies and wallets unlawfully obtained. Details are fuzzy, but experts like Tom Kemp from Centrify told Forbes that he wouldn’t be surprised if it was a result of badly managed “identity and access”. Kemp points out in that same piece that “[t]he traditional cybersecurity approach of ‘trust, but verify’ simply does not work in today’s mobile-first, a cloud-enabled world where employees can be anywhere and working on multiple devices.”
Technology & Risk Management with LeanIX:
Again, it all boils down to practical standards of governance. LeanIX’s collaborative approach to inventorying IT applications empowers security and compliance officers to maintain up-to-date overviews of software—whether company-sanctioned or not. As seen in the below image, an IT Component Landscape Report displays software and hardware assets in use throughout an enterprise, at varying hierarchy levels, alongside their corresponding levels of compatibility.
Image 5: A LeanIX IT Component Landscape Report showing software and hardware assets in use throughout an operation.
Exactis — 340 million
What Happened: Exactis, a US-based marketing firm, exposed 340 million individual records of citizens and businesses on a publicly accessible server. The failure is said to have been spotted before it was abused, however. It’s simply another case of a user database accidentally being made accessible to the public—an issue that has reached epidemic levels according to Wired.
Technology & Risk Management with LeanIX:
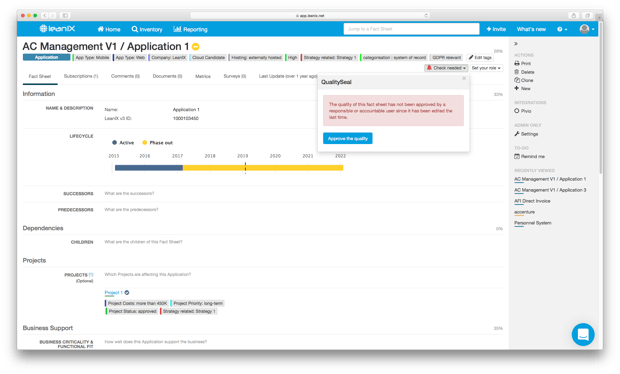
The LeanIX “Quality Seal” is an integral mechanism of the EA Management Tool used to prevent security protocols from slipping into irrelevance. Quality Seals appear on the top right of a “Fact Sheet” (a.k.a., the building blocks of the LeanIX analytics and inventory network), and if the information is past its review date, the seal will “break” and an automated action call will be sent to all responsible parties to initiate immediate repair.
Image 6: A LeanIX "Quality Seal", in frame, alerting users to the need for a data quality review.
Aadhar — 1.1 billion
What Happened: The Indian Government’s national identification registry—Aadhaar—was (to put it mildly) compromised. More than 1.1 billion bits of data capable of helping criminals assume identities with remarkable precision were stolen. A great deal is being denied by government sources, but the prevailing narrative is that a vulnerability on a separate state-owned system functioned as a backdoor into the Aadhaar network.
Technology & Risk Management with LeanIX:
LeanIX endorses and offers the necessary functionality to complete a 5-step approach to Technology Risk Assessment. As follows:
- Get a complete list of the applications in use
- Assess software versions in use
- Assess servers and data centers in use
- Define the links between software and servicers to IT applications
- Analyze how technology affects your business
It's a plan that's contributed to the success of many LeanIX customers. But if you'd like to have more information on how it works, or if you just simply want to discuss its logic in better detail, just reach out to me via social media or e-mail. Everyone on my end is always willing to give a commitment-free demo of our Enterprise Architecture Management Tool.